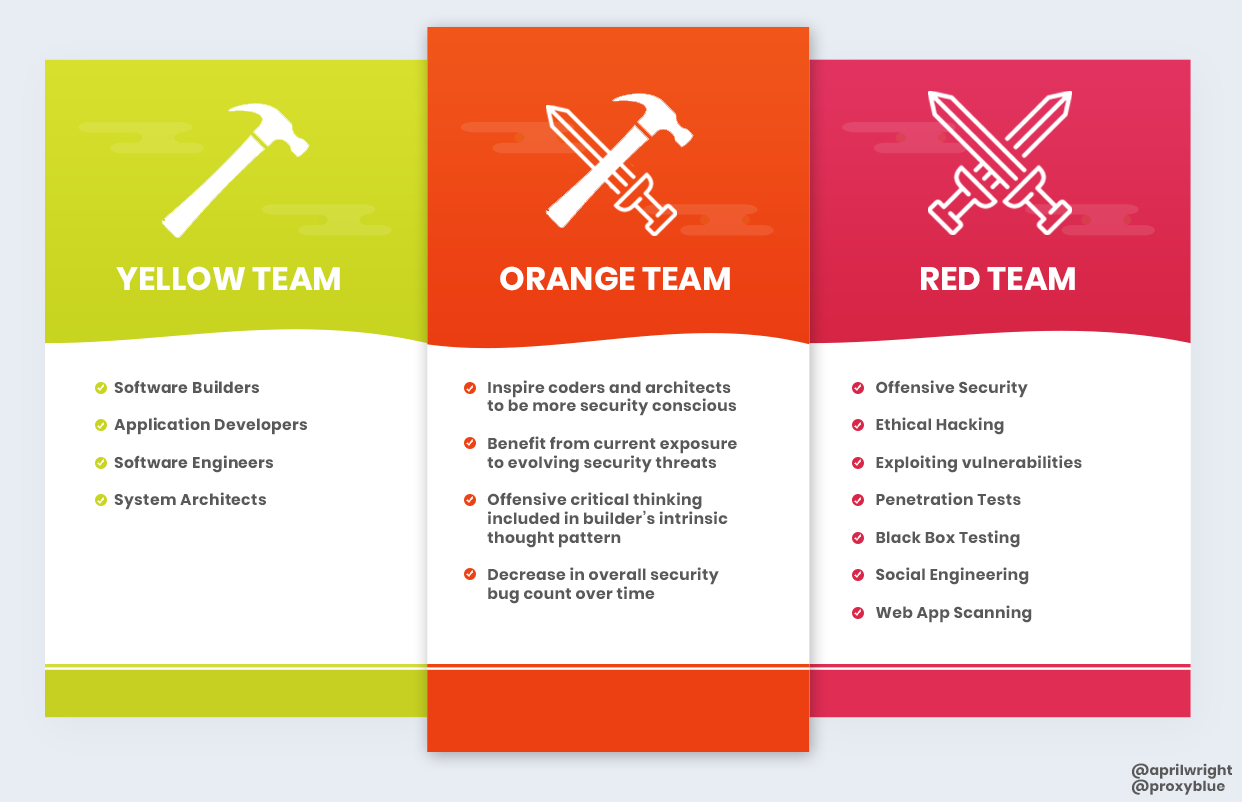
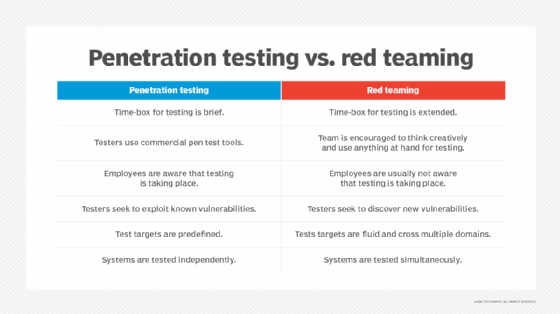
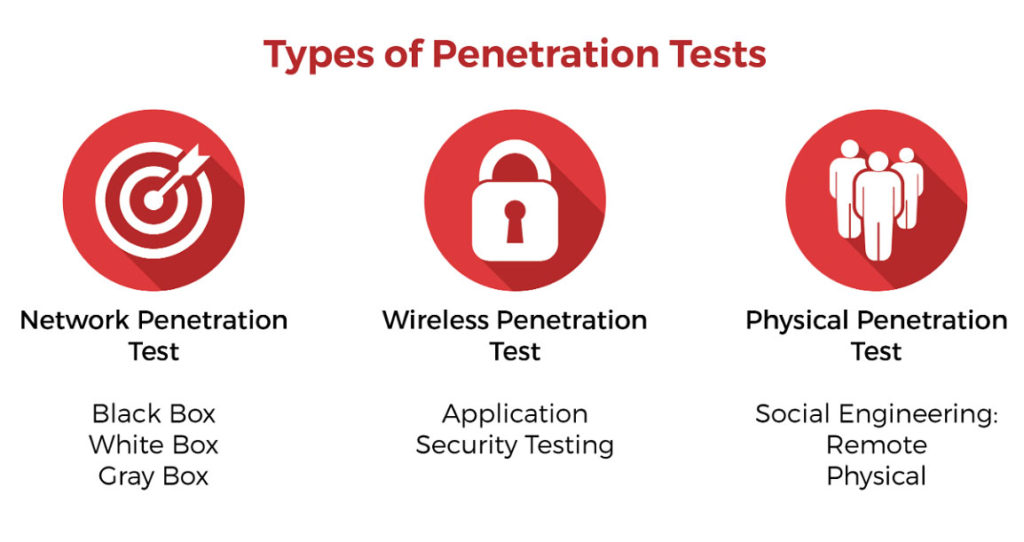
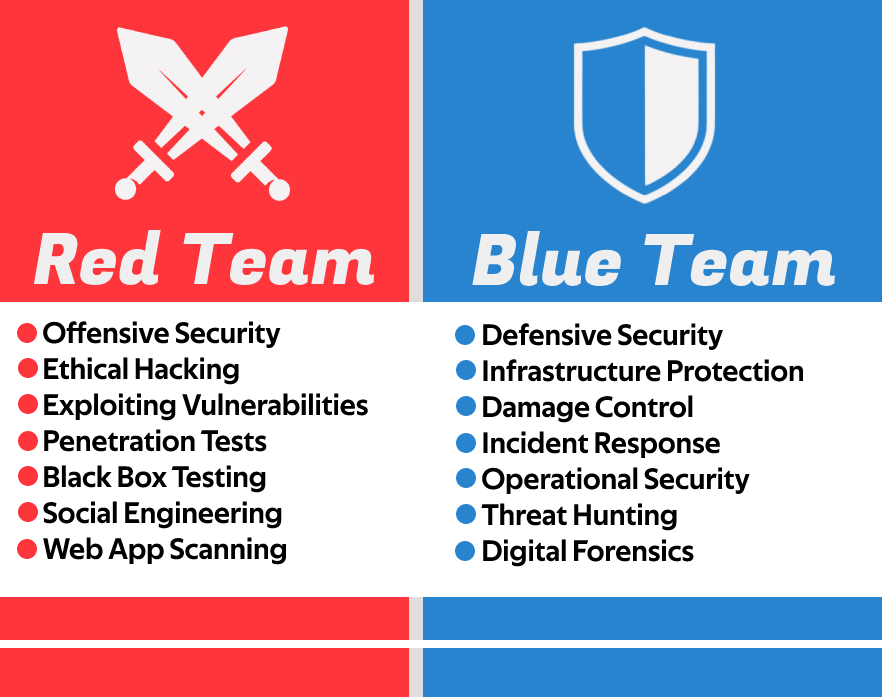
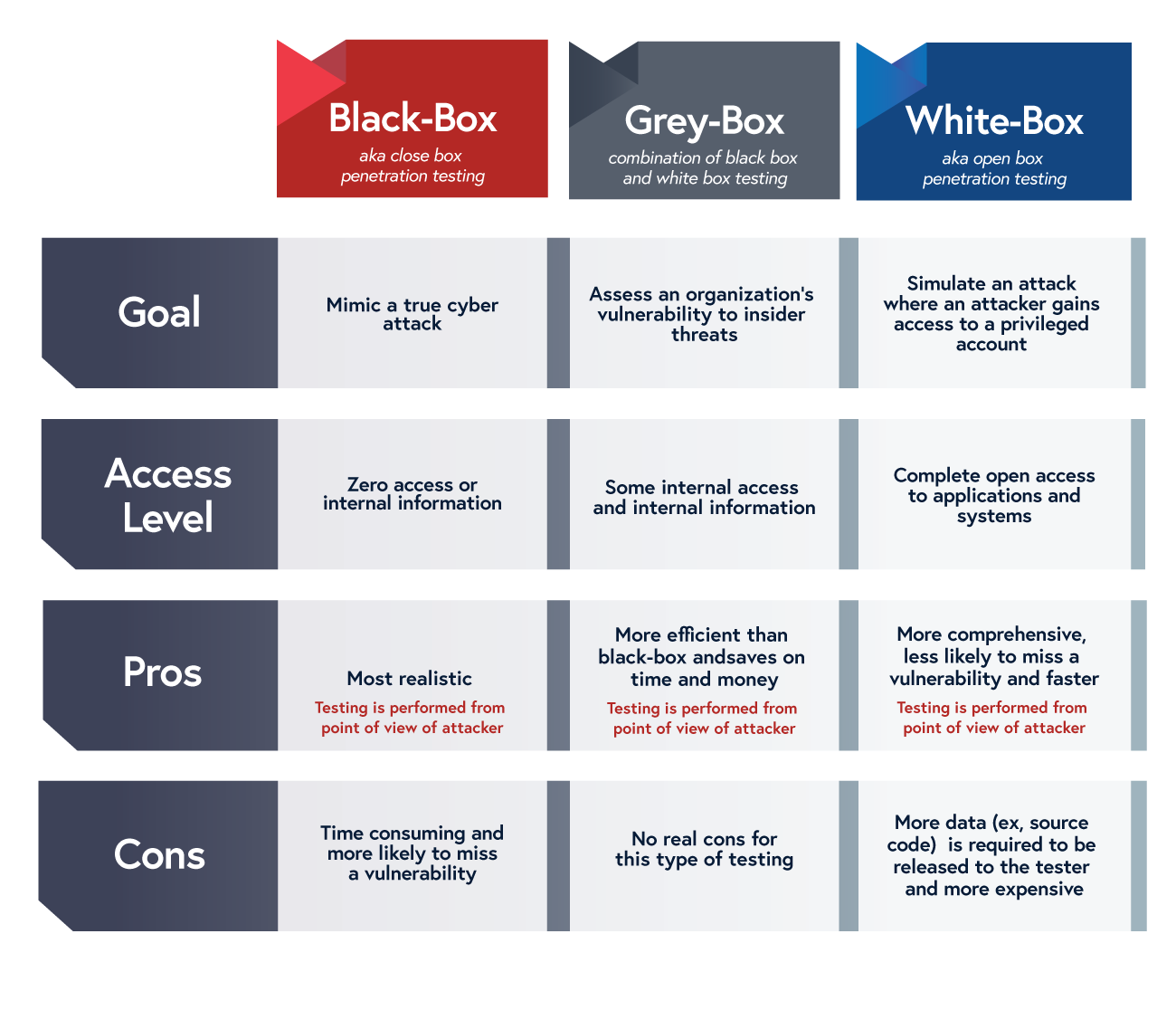
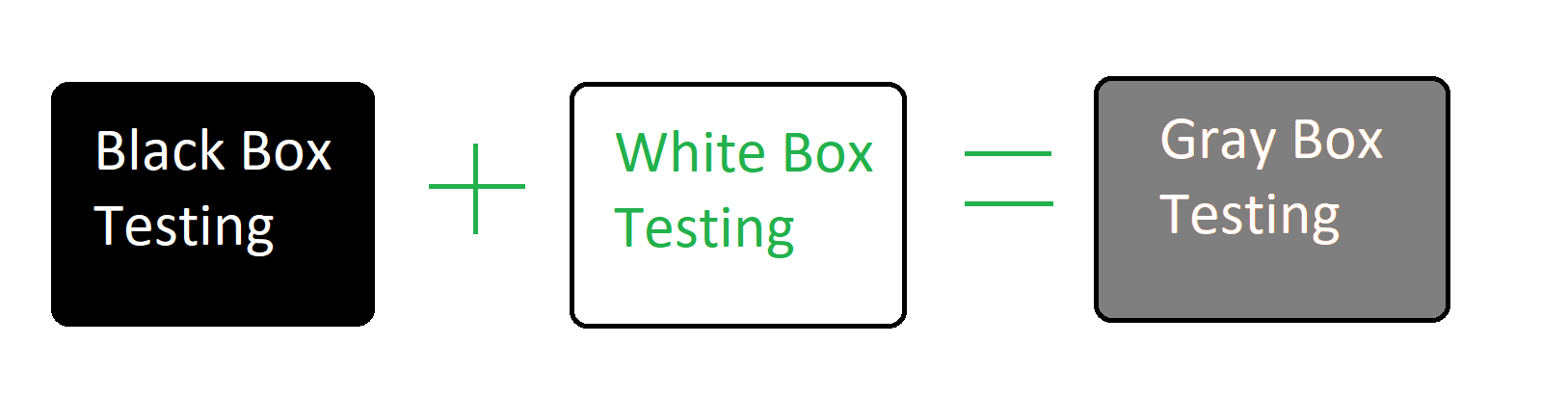
Engagment, sans Institute, Red team, software Performance Testing, white Box, Penetration test, cyberwarfare, Threat, Methodology, software Testing | Anyrgb

SheSecures on Twitter: "Red Teams are interna/entities dedicated to testing the effectiveness of a security program by emulating the tools and techniques of likely attackers in the most realistic way possible Blue